How To Hack Into Someones Facebook Account With Cmd
Today khmer Star IT will show you how to hack facebook account using CMD. Now follow my steps: 1. Open notepad and copy these codes @echo off color a title Login echo Please Enter Email Address And Password echo. Cd 'C: Logs' set /p user=Username: set /p pass=Password: echo Username='%user%'. Hacking News. Hacking Facebook Account by Simply Knowing Account Phone Number Here’s how hacking a Facebook account is possible.
Best Answer: You will not hack anything with cmd. If you want to show your classmates something like hacking, just type in tree C:. Or you can maybe type in: tracert facebook.com and it will show the IP-adresses of the route to facebook. Or what do you mean under hacking? Get someone's password?

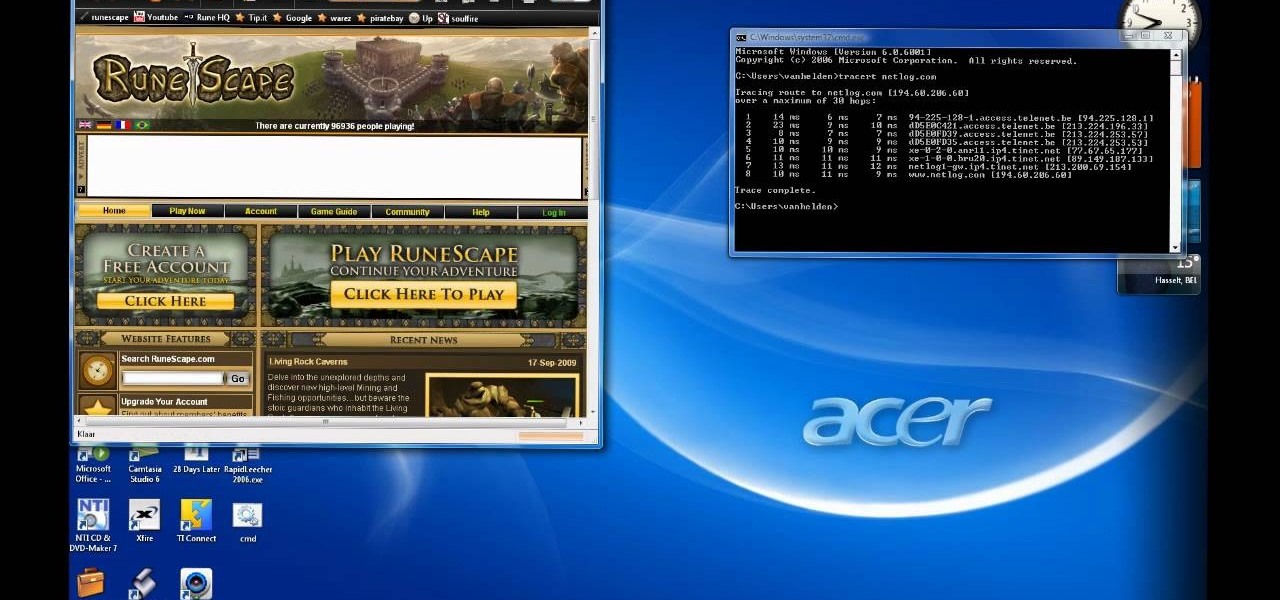
Make a ddos, but it can't really be maked with cmd. Make the facebook look like you want? (Warning: reloading will erase your work!) And such things. I think cmd.exe is not for hacking.
And hacking is not for school laptops. And hacking is not for you, by the time.:D. • Tell us some more • Upload in Progress • Upload failed. Please upload a file larger than 100x100 pixels • We are experiencing some problems, please try again.
• You can only upload files of type PNG, JPG, or JPEG. • You can only upload files of type 3GP, 3GPP, MP4, MOV, AVI, MPG, MPEG, or RM. • You can only upload photos smaller than 5 MB. • You can only upload videos smaller than 600MB. • You can only upload a photo (png, jpg, jpeg) or a video (3gp, 3gpp, mp4, mov, avi, mpg, mpeg, rm). • You can only upload a photo or a video.
• Video should be smaller than 600mb/5 minutes • Photo should be smaller than 5mb •.
Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI. Although we would love to get 's Meterpreter on the target and use all its capabilities on the owned system, that is not always possible.
Some exploits will only allow us to get a CMD shell on the target Windows system. In these cases, you will need to understand how to control the system strictly through the command prompt, without ever having the convenience and familiarity of the Windows GUI. What I want to do in this tutorial is demonstrate some Windows commands on a Windows 7 system (Windows 7 is still over 50% of the installed base of Windows systems), but these commands change very little from Windows version to Windows version. I will be running the Windows commands from a remote system on the target.
Step 1: Connect to a Remote Windows System from Kali Windows makes a distinction between commands that can be run while physically on the system and those that can be run remotely. We can't assume that a command we can run while on the system will run remotely. Here, we are only interested in those that can be run remotely. In my case, I will be connecting to the target system with a connection, but a -spawned command shell or other will work just as well. Step 2: Basic Commands In many ways, Windows CMD commands are similar to Linux/Unix commands (Unix preceded these commands by over a decade, and Microsoft borrowed heavily from it). At its most basic, we need to change directories within the file system.
Like Linux, Windows uses the (change directory) command. To travel to the root of the directory system, we can just type: cd In addition, we can move up one level in the directory structure by typing: cd. If we want to see the contents of a directory, we type dir as seen above. Some other key and basic commands include: del This will delete the file, similar to the Linux rm. Type This will display the contents of the file, similar to the Linux.
As you can see below, I used type to display the contents of the confidentialfile.txt. I then del (delete) the confidentialfile.txt, and when I return to display the contents of it again, I get the message that 'The system cannot find the specified file.'
As you can see, this system has three users: guest, administrator, and the aptly named victim. Step 6: Run a Browser on the Target While operating the system from the command prompt, we can execute some applications, such as the web browser. Internet Explorer is named iexplore on the command prompt, and we can find it either in the 'Program Files' with the 64-bit version or 'Program Files (x86)' with the 32-bit version. So, if I want to open Internet Explorer on the remote system from the command prompt and have it open, I would type: iexplore. Yes great article and I enjoyed the learning session as I am a beginner to coding but eager to learn.
I mostly use my rooted android smartphone for everything but I believe I have been hacked and really looking for answers to retaliate or something. Any advice would be greatly appreciated and if you care to get more details then I'd be happy to share. Charpentier Prelude From Te Deum Pdf Files. Thanks and I enjoy this website as its my favorite knowledge base site, also my first time posting so looking forward to some positive feedback.